Solutions
Android Application Development
IOS Application Development
Flutter Application Development
React Native Application Development
Progressive Web App
Responsive Web App
e-Commerce Website Development
ERP Development
CRM Development
Data Visualization
Product Design
Project Management
Artificial Intelligence
Block Chain
Cryptocurrency
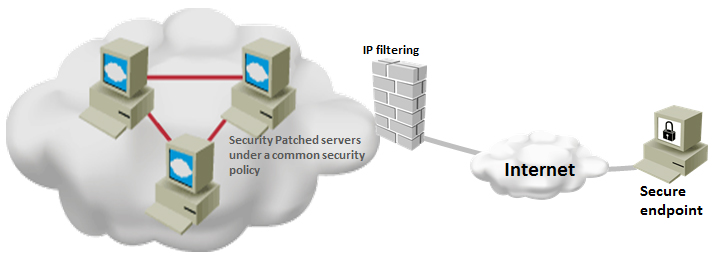
Cyber Security
SMO
SEO